RSC Explorer; Cloudflare Error Page Generator; SQL Quest: The Bank Job
I spent much of Q3 and early Q4 revamping my CMU course. I gave said lecture this past week, and the work for that, along with the need to spend an inordinate amount of time tracking React2Shell nonsense has made December Drops pretty sparse.
If you’re interested in “data-driven threat intelligence” or just cyber-curious, this repo has “A Practical Guide to Cyber Threat Intelligence” and “Operationalizing CTI: Considerations for Security Leaders”. They’re two additional resources I developed for the course, since I found other threat intel content was not really aimed at security leaders (existing or budding ones). Full Typst + Markdown sources are available.
I also finally carved out time to finish up and publish a thinkpiece/essay/whitepaper titled “Children Of The MagentAI” which contains a critical analysis of automation dependency patterns in modern cybersecurity and software development, drawing parallels to aviation’s “magenta line” phenomenon.
(So, I have definitely not been slacking off. 🙂
Today, we have three pretty diverse resources for y’all to ponder. Yes, the “exploits” does have something to with React2Shell, but it’s a super cool way to learn some front-end skills as you also learn more about RSC and how to hack things.
TL;DR
(This is an LLM/GPT-generated summary of today’s Drop. This week, I have been — for lack of a better word — forced into using Gemini, so today’s summary was provided by that model. Sigh. This is also the last Drop that will be using Gemini for the TL;DR.)
- Dan Abramov’s RSC Explorer provides a hands-on, client-side tool to visualize the React Server Components protocol and understand security vulnerabilities like CVE-2025-55182 (https://rscexplorer.dev/).
- The Cloudflare Error Page Generator by Anthony Donlon allows users to create fast-loading, customized error pages that mimic Cloudflare’s design to humorously shift blame for site downtime (https://virt.moe/cferr/editor/).
- SQL Quest: The Bank Job offers a gamified detective story where players solve a robbery by writing complex SQL queries against realistic, messy data to sharpen their analytical skills (https://www.sqlhabit.com/quests/the-bank-job).
RSC Explorer
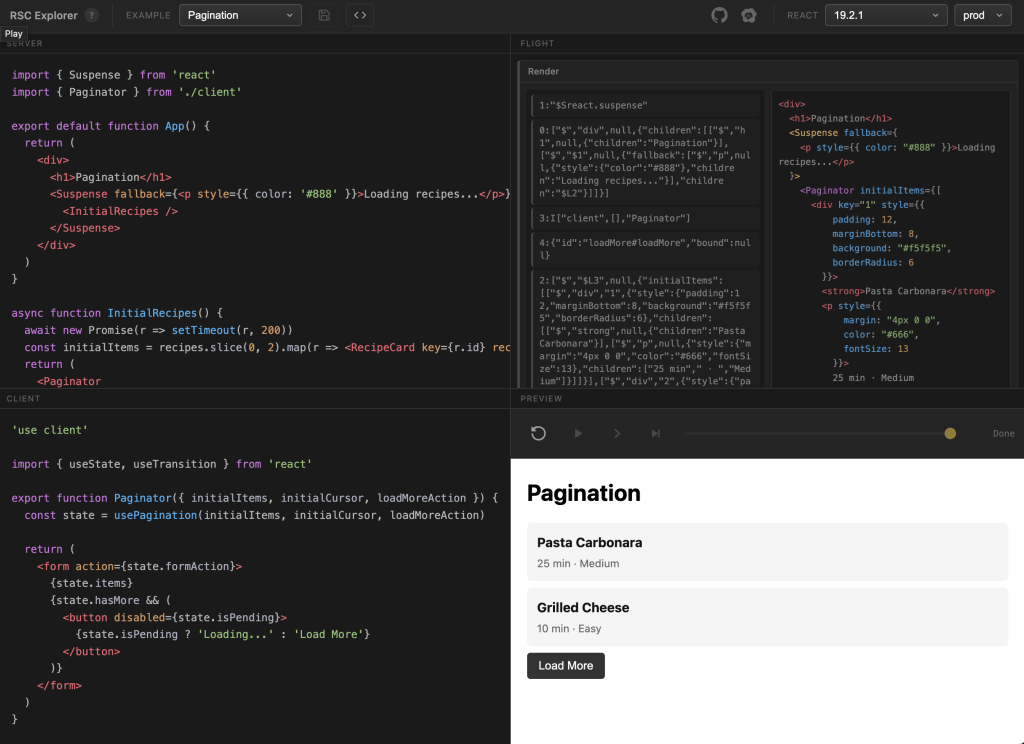
Dan Abramov just dropped something genuinely useful for anyone trying to understand what actually happened with the React Server Components vulnerability I keep blathering about and that we’ve been tracking at work. His RSC Explorer (GH) is designed to show how the exploits work under the hood, and has full source for you to play with and expand upon.
If you’ve been following the React2Shell situation at all, you know that CVE-2025-55182 caused a lot of confusion. Part of that confusion stems from the fact that most developers using React Server Components don’t really understand the protocol that makes RSC tick. It’s an implementation detail that React intentionally doesn’t document heavily, which gives the React team flexibility to evolve it, but also means that when something goes wrong, people are left scrambling to understand what they’re even looking at.
React2Shell exploited a flaw in how the RSC protocol handles certain payloads, allowing attackers to achieve remote code execution on vulnerable servers. We saw thousands of exploitation attempts in the wild, with threat actors probing for vulnerable Next.js and other RSC-enabled applications. The vulnerability was serious enough that it drew comparisons to Log4Shell, and while the scope was different, the urgency was real.
Dan’s Explorer lets you step through the RSC protocol in your browser. The whole thing runs client-side, with the server portion running in a web worker, so you’re not making any network requests. But it uses the actual React packages that read and write the RSC protocol, so everything you see is real.
The way it works is pretty clever. You write some server and client code in the left pane, and then you can step through the execution one chunk at a time. You see the raw protocol output, the JSON-like format that React uses to serialize component trees, and then you see what the client reconstructs from that data. It makes visible what’s normally invisible.
There’s even a specific example for CVE-2025-55182, though you have to select version 19.2.0 in the corner to see it work since that was the vulnerable version. Being able to actually watch the exploit flow through the protocol is educational in a way that reading about it just isn’t.
Beyond the security angle, the tool is just a really nice way to build intuition for how RSC actually works. You can watch streaming in action, see how Suspense boundaries create “holes” that get filled in as data arrives, understand how client components get referenced rather than having their code sent over the wire, and see how server actions work in the opposite direction. There’s an example showing how a router refresh works without a framework, which demystifies a lot of the magic that Next.js and similar frameworks provide.
As noted, the source is available on GitHub if you want to dig into how he built it, and the whole thing is embeddable so you can include live examples in your own documentation or blog posts.
If you’re doing any work with RSC, or if you’re just curious about what was actually happening with React2Shell at the protocol level, I’d encourage you to spend some time with this and the blog post walking through it.
Cloudflare Error Page Generator
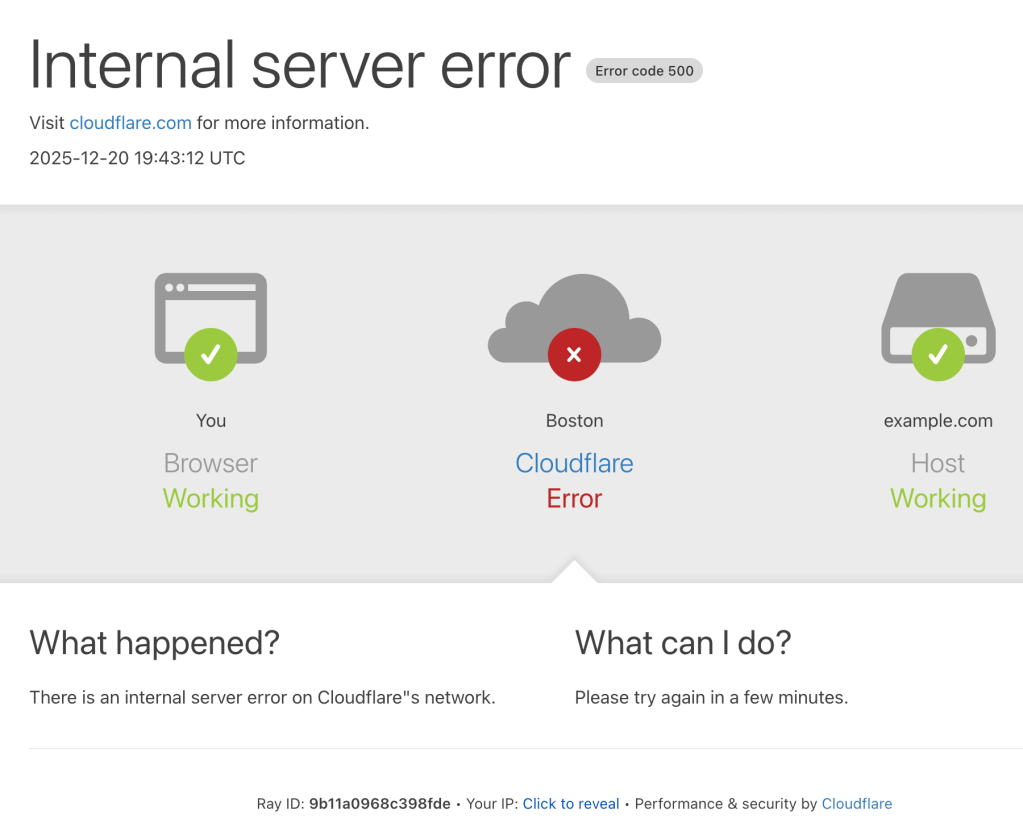
This definitely made the rounds, but it deserves some preservation in the Drop.
Cloudflare is one of the most harmful and evil corporations to have ever existed. It’s one of those “you have to be a sociopath to work there” kind of places, and they’ve likely irreparably harmed what was the open internet. Some of you will also remember they took down most of said internet a couple times in the past few weeks.
This project (GH) by Anthony Donlon creates customized error pages that mimics the very well-known Cloudflare error page. You can also embed it into your website, and put the blame on them when your own site goes down (but that may send a signal you use Cloudflare, which I would be somewhat embarassed to even remotely have errantly associated with me).
The editor is super-easy to use, and the pages do not load any other static resources, so they are served up super fast, unlike all the sites Cloudflare took down this past year due to sheer incompetence.
There are some examples you can poke through to see what’s possible in terms of customization, and the sources for the editor and pages themselves are very grok-able, especially if you’re looking to get better at javascript/typescript.
SQL Quest: The Bank Job
I do code “katas” all the time to keep concepts and syntax fresh in active, human RAM. While I tend to do this with practical mini-projects, there are times I find it a bit more fun when there’s gamification involved, especially when it’s framed as a mystery to solved (we’ve covered more than a few of these types of things in previous Drops).
Either this week or last week I came across a neat way to practice SQL that doesn’t feel like practice at all. SQL Habit just released something called SQL Quest, and the first one is called “The Bank Job.” The premise is simple: a bank has been robbed, and you’re the detective. Your job is to follow the trail of evidence through the bank’s database, figure out what happened, and ultimately help Interpol catch the thief. You solve puzzles by writing SQL queries, and each chapter teaches you something new while advancing the story.
Most SQL tutorials teach you syntax in isolation. You learn how to write a JOIN or a window function, but you’re working with clean, obvious data where the answer is basically handed to you. Real data work is 100% definitely NOT like that. Real data work is messy and ambiguous, and you have to figure out what question to even ask before you can write the query to answer it.
The Bank Job uses realistic, messy data and gives you context and clues instead of step-by-step instructions. You have to turn those clues into insights, which is much closer to actual data analysis work. The creator, Anatoli Makarevich, comes from a background building startups and working on growth and BI at Blinkist, so he’s clearly seen the difference between textbook SQL and the kind of SQL you actually need to get things done.
The whole thing takes somewhere between 20 minutes and an hour depending on your skill level. If you can write window functions without looking anything up, you’ll breeze through it. If you’re still building those muscles, plan for the longer end and use it as a learning opportunity. Each chapter has three levels of hints if you get stuck, though using them adds time penalties if you’re competing for the leaderboard.
It’s completely free and doesn’t require a credit card or bitcoin wallet. If you’re looking for a way to sharpen your SQL skills that’s more engaging than working through another set of exercises about employees and departments, this seems like a pretty spiffy option.
FIN
Remember, you can follow and interact with the full text of The Daily Drop’s free posts on:
- 🐘 Mastodon via
@dailydrop.hrbrmstr.dev@dailydrop.hrbrmstr.dev - 🦋 Bluesky via
https://bsky.app/profile/dailydrop.hrbrmstr.dev.web.brid.gy
☮️
Leave a comment