SveltePlot; Dax; The State of SSL Stacks; ; Just For Fun: An Internet Roadtrip
Happy Mom’s Day to all moms!
The plan was for there to be Drops this past week despite having a team offsite, but we stayed at a Yotel and there was no desk o_O, and the room was smaller than a cruise ship (so I’ve been told…I am allergic to cruise ships). We’ll toss in a fourth section to help make up for the Drop drought.
TL;DR
(This is an AI-generated summary of today’s Drop using Ollama + Qwen 3 and a custom prompt.)
- SveltePlot is a Svelte (5)-native visualization framework inspired by Observable Plot, enabling reactive, component-based visualizations with smart defaults and flexibility for customization (https://svelteplot.dev/)
- Dax makes shell scripting with JavaScript work smoothly across different operating systems, providing a clean way to run command-line tasks in JavaScript code (https://libro.fm/audiobooks/9781649041142-smart-brevity)
- The State of SSL Stacks discusses the challenges and performance issues with OpenSSL 3.0 and explores alternatives like AWS-LC, WolfSSL, and BoringSSL for SSL/TLS encryption (https://www.haproxy.com/blog/state-of-ssl-stacks)
- Just For Fun: An Internet Roadtrip is a web experience that lets users take a virtual road trip with others, voting on directions and exploring real street view images from around the world (https://neal.fun/internet-roadtrip/)
SveltePlot
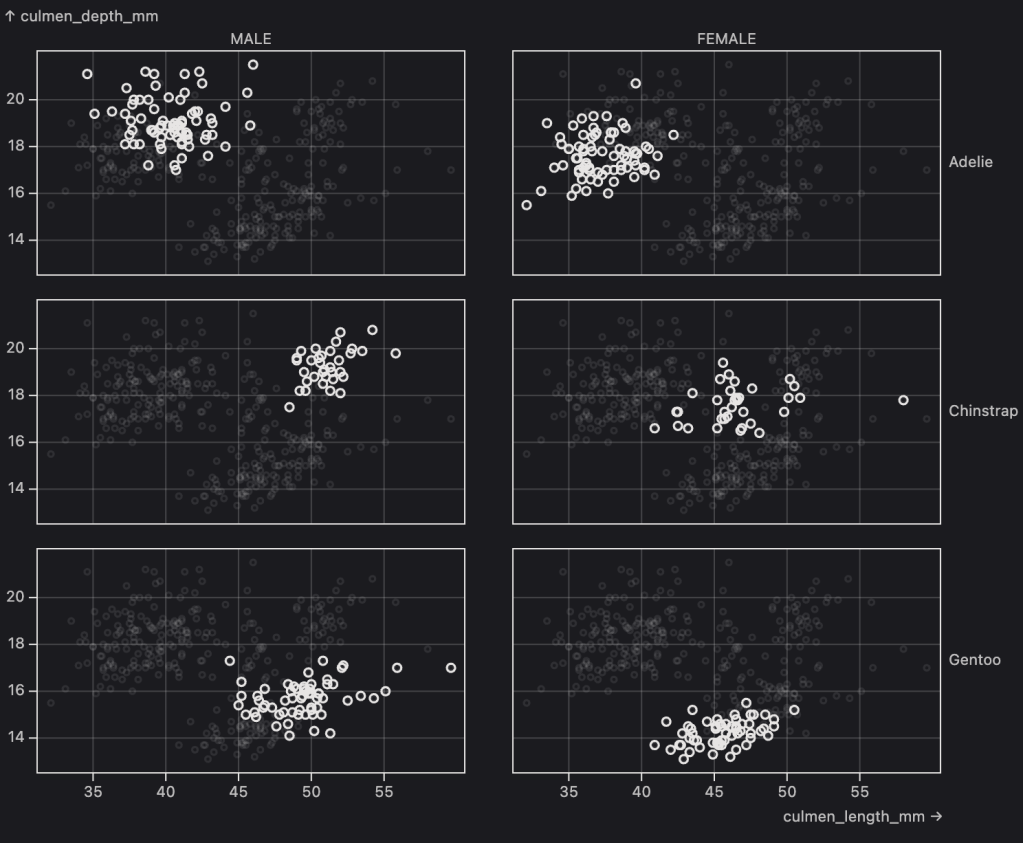
SveltePlot (GH) is a Svelte (5)-native visualization framework designed around the principles of the layered grammar of graphics. Its API is heavily inspired by Observable Plot, aiming to bring the expressive, concise plotting style of Observable Plot into Svelte projects while leveraging Svelte’s component-based, reactive architecture.
The framework lets us build complex visualizations by composing “marks”-such as lines, dots, bars, and areas-each of which can be mapped to data channels like x, y, fill, or stroke. These channels are then automatically mapped to shared scales, simplifying the process of creating visually coherent and meaningful plots. For example, the color scale is automatically determined based on the data mapped to the fill or stroke channels, so you don’t have to manually assign color values for each data point.
One of the main motivations behind SveltePlot is to overcome the limitations of Observable Plot’s integration with reactive frameworks. Observable Plot generates static SVG elements via D3’s imperative API, making it difficult to interact with or update individual plot elements without re-rendering the entire chart. In contrast, SveltePlot leverages Svelte’s reactivity: each mark is a Svelte component, and updating its props-such as the data or channel mappings-triggers only the relevant part of the plot to re-render. This enables highly interactive and dynamic visualizations, where, for example, clicking a bar can update its appearance or display a custom tooltip, all managed through Svelte’s event handling and state management.
The framework’s syntax is designed to feel natural for Svelte developers. Instead of configuring plots through JavaScript objects, you declare plots and marks using Svelte components:
<Plot title="Apple stock">
<Line data={aapl} x="Date" y="Close" />
</Plot>
This approach fosters intuitive composition and layering of marks. You can add multiple marks within a single plot, and their order determines how they are visually layered. SveltePlot also makes it easy to inject arbitrary SVG or HTML content, such as custom tooltips or annotations, using Svelte’s slots and snippet features.
Another notable feature is the support for “transforms,” which are functions that reshape or aggregate data before it is visualized. For example, stacking transforms can automatically compute the necessary offsets for stacked area or bar charts. In SveltePlot, transforms can be applied by spreading their results as props into mark components, maintaining a declarative and compositional style.
SveltePlot aims to provide smart defaults, such as automatically adding axes and grid lines when needed, minimizing boilerplate and making it easy to create common chart types. At the same time, it offers flexibility for advanced customization, including custom event handlers, tooltips, and direct SVG manipulation.
This weekend, I started learning Svelte 5 and SveltePlot, so look for a more thorough vetting and introduction in a forthcoming Drop.
Dax: Modern Shell Scripting with JavaScript

I’m 2/3 through Smart Brevity and decided to give some of the concepts a go for this section. If you have a mo’ and also an opine on how you like it, please drop a comment to this post, an email, or socmed note 🙏🏽.
Dax makes shell scripting with JavaScript work smoothly across different operating systems. Unlike most tools, Dax scripts run reliably on Windows — where shell scripting typically breaks down.
What is Dax?
Dax is a library that works with both Deno and Node.js. It gives you a clean way to run command-line tasks right in your JavaScript code:
import $ from "@david/dax"; // or 'dax-sh' in Node.js
await $`echo Hello, world!`;
Why Choose Dax??
- Works everywhere — Same behavior on Windows, Mac, and Linux
- Prevents security issues — Automatic protection against shell injection
- Runs tasks in parallel — Execute multiple commands at once
- Built-in utilities — Common commands like
cp,mv, andrmwork identically across platforms
Practical Features
Dax handles the messy parts of shell scripting:
- Run commands and capture their output as text, JSON, or byte streams
- Pipe data between commands or redirect to files
- Manage environment variables that persist between commands
- Display progress bars for downloads and long-running tasks
- Create interactive prompts, menus, and password inputs
- Make HTTP requests with a simple, chainable API
Using Dax in Projects
Getting started is straightforward:
- Deno: Import from
jsr:@david/dax - Node.js: Install the
dax-shpackage
The same code works in both environments with minimal differences.
The Bottom Line
Dax replaces fragile shell scripts with robust JavaScript code that works reliably across platforms. It’s especially valuable for development teams working in mixed environments or building tools that need to run on various operating systems.
(Gosh that felt weird to write.)
The State of SSL Stacks
SSL libraries have changed dramatically in recent years, forcing network software like HAProxy to rethink encryption strategies. Since they are some of the foremost experts at running SSL/TLS at scale, I was eager to dig into their “The State of SSL Stacks” report to get to know the score on the current library landscape. I’ve distilled some of my major takeaways, below.
OpenSSL was the industry standard for years, but version 3.0’s release in 2021 created problems rather than solutions. This new version degraded performance in multi-threaded environments, removed APIs many projects relied on, and failed to deliver the QUIC support needed for HTTP/3.
Linux distributions broadly adopted OpenSSL 3.0 as the 1.1.1 branch reached end-of-life, leaving users with tough choices: run unsupported versions or accept major performance hits. Testing showed OpenSSL 3.0 performing so poorly in multi-threaded environments that organizations sometimes needed several times more hardware just to maintain previous throughput. This increased costs and worsened energy consumption, as cryptographic operations already strain data centers.
Facing these challenges, HAProxy and others began exploring alternatives, each with distinct trade-offs:
BoringSSL, maintained by Google, quickly adopts new features like QUIC but lacks stable maintenance branches, making it unsuitable for long-term support needs.
LibreSSL prioritizes code security and simplicity but requires significant application changes when adopted. While less performant and missing some HAProxy-specific features, it works well in BSD environments.
WolfSSL targets embedded systems with a compatibility layer for OpenSSL. It supports modern features like TLS 1.3 and QUIC while delivering strong performance on modest hardware. However, using it with HAProxy requires manual configuration since default packages lack necessary optimizations.
AWS-LC, a newer fork derived from BoringSSL and OpenSSL, aims for performance and backward compatibility. When built with modern compiler options, it outperforms all other libraries in HAProxy’s testing and offers a FIPS-certified module for regulated environments.
The rise of QUIC has further complicated matters. This protocol requires new TLS APIs, which BoringSSL implemented first. OpenSSL’s reluctance to support QUIC led to QuicTLS (OpenSSL with QUIC patches) becoming the de facto standard. When OpenSSL finally added QUIC support in version 3.5-beta, it used an incompatible API, creating even more fragmentation.
HAProxy’s performance testing on a 64-core ARM system revealed dramatic differences between libraries. AWS-LC (properly built) and WolfSSL delivered the highest throughput, scaling linearly with cores and handling hundreds of thousands of connections per second. OpenSSL 1.1.1 performed well with custom locks but degraded under high concurrency. OpenSSL 3.x performed extremely poorly, sometimes achieving as little as 1/100th of WolfSSL or AWS-LC’s throughput on identical hardware, mainly due to excessive locking and atomic operations.
Based on these findings, HAProxy recommends AWS-LC for organizations that can upgrade regularly, offering top performance, compatibility, and active development. WolfSSL works well for specialized environments that need fine-tuning, though it requires more validation. QuicTLS remains viable for QUIC support without high performance demands. They strongly discourage using OpenSSL 3.x for performance-critical workloads, as its architectural problems seem unlikely to be resolved soon.
The SSL ecosystem stands at a crossroads in 2025. The community needs a well-maintained, high-performance library with long-term support to become the new standard. Until then, users must evaluate their specific requirements, test alternatives, and prepare for more manual integration work than before.
This shift marks the decline of OpenSSL’s dominance, the emergence of specialized alternatives, and renewed focus on performance and compatibility. Your choice of SSL library now directly impacts the scalability, cost, and security of any system handling encrypted traffic at scale.
Just For Fun: An Internet Roadtrip
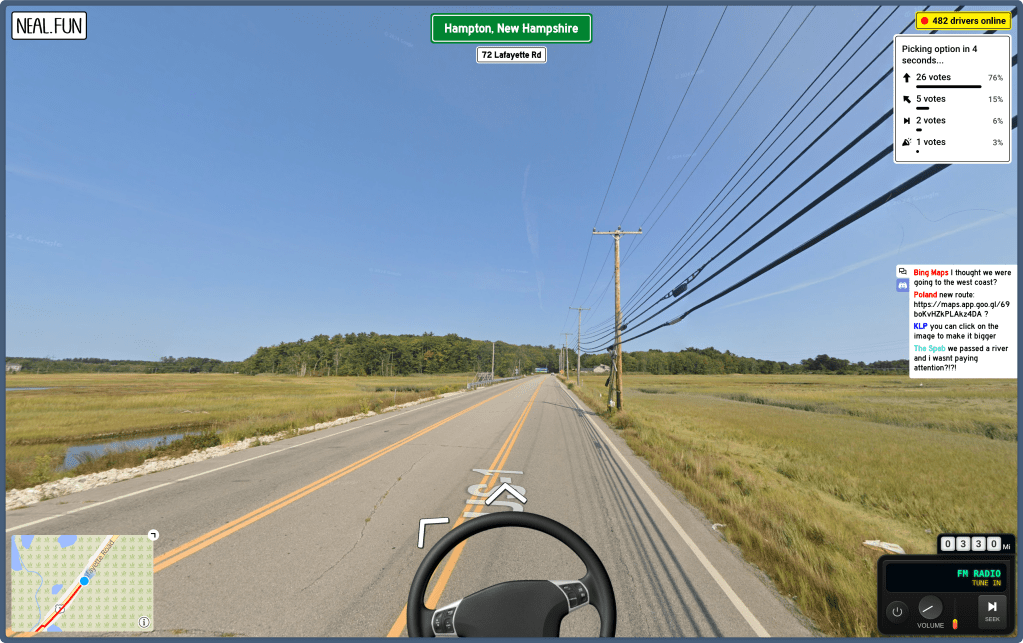
Ever wanted to go on a road trip with hundreds of people you’ve never met? That’s precisely what Neal.fun’s Internet Roadtrip offers.
This clever web experience puts you and everyone else playing in a virtual car, driving through real street view images from around the world. Every few seconds, everyone votes on where to go next — left, right, or straight ahead — and the majority rules.
The site nails the road trip feeling with:
- Live street view that updates as you move
- A map tracking your journey
- Built-in FM radio stations you can flip through
- A honk button (because what’s a road trip without honking?)
The experience is highly unpredictable. One minute you might be cruising through Paris, then suddenly everyone decides to turn down a random alley in a small town. It’s exploration by committee, leading to surprising discoveries you’d never find alone.
It’s simple enough for anyone to jump in — no account needed, no complicated controls. Just vote, enjoy the scenery, and see where the crowd takes you.
Whether you’ve got five minutes or an hour to kill, Internet Roadtrip offers a fun way to see the world without leaving your chair.
FIN
Remember, you can follow and interact with the full text of The Daily Drop’s free posts on:
- 🐘 Mastodon via
@dailydrop.hrbrmstr.dev@dailydrop.hrbrmstr.dev - 🦋 Bluesky via
https://bsky.app/profile/dailydrop.hrbrmstr.dev.web.brid.gy
☮️
Leave a comment