The Non-existent Xiaohongshu (小红书/REDnote) BACKDOOR; Don’t Be Too Quick With Google Search Results And/Or curl|bash; Cooked.Wiki Redirector(s); Upgrade Vite & Redeploy Apps That Use The Dev Server
Today’s Drop is a compendium of items from the weekend(ish) that warrant attention, but that don’t fit into the normal Drop idiom. A few are security-related, and one is a quality-of-life improvement for something we Dropped a couple weeks ago.
Remember to turn off the news, today!
TL;DR
(This is an AI-generated summary of today’s Drop using Ollama + llama 3.2 and a custom prompt.)
- Xiaohongshu’s alleged “backdoor” is actually a benign feature-loading mechanism common in Chinese software development, with transparent plugin management and auditable implementations (https://remyhax.xyz/posts/xiaohongshu-rednote-backdoor/)
- Malicious Google Ads are impersonating legitimate software installers like Homebrew and Arc, highlighting the importance of verifying installation sources (https://xcancel.com/ryanchenkie/status/1880730173634699393)
- A browser extension and iOS shortcut have been created to simplify accessing recipe content through Cooked.Wiki’s URL prepending feature (https://codeberg.org/hrbrmstr/cw-ext)
- Critical security vulnerabilities in Vite’s development server require immediate upgrade to versions 6.0.9, 5.4.12, or 4.5.6 to prevent source code theft and server exploitation (https://github.com/vitejs/vite/security/advisories/GHSA-vg6x-rcgg-rjx6)
The Non-existent Xiaohongshu (小红书/REDnote) BACKDOOR

Fellw $WORK team member and all around awesome human Remy took time out of his personal life to set the record straight about the FUD surrounding a potential backdoor in the app U.S. TikTokians are jumping ship to.
Chinese social media app Xiaohongshu (小红书/REDnote) recently made headlines when someone spotted the word “backdoor” in its code, raising security concerns. After thorough analysis of both iOS and Android versions, these “backdoors” turn out to be benign feature-loading mechanisms common in Chinese software development. The Android implementation uses it for plugin management to handle different device capabilities, while the iOS version employs it for feature toggling in the view controller, particularly around payment processing. The terminology appears to be a cultural/linguistic artifact rather than anything nefarious, as similar usage appears even in Microsoft’s Mandarin documentation.
The plugin system maintains a SQLite database of all loaded modules, making them easily auditable, and the iOS implementation focuses on scope changes for secure transactions. All plugin activities can be monitored via standard Android debugging tools without requiring root access.
Remy’s post is a tad on the technical details side, but well worth the 👀.
Don’t Be Too Quick With Google Search Results And/Or curl|bash
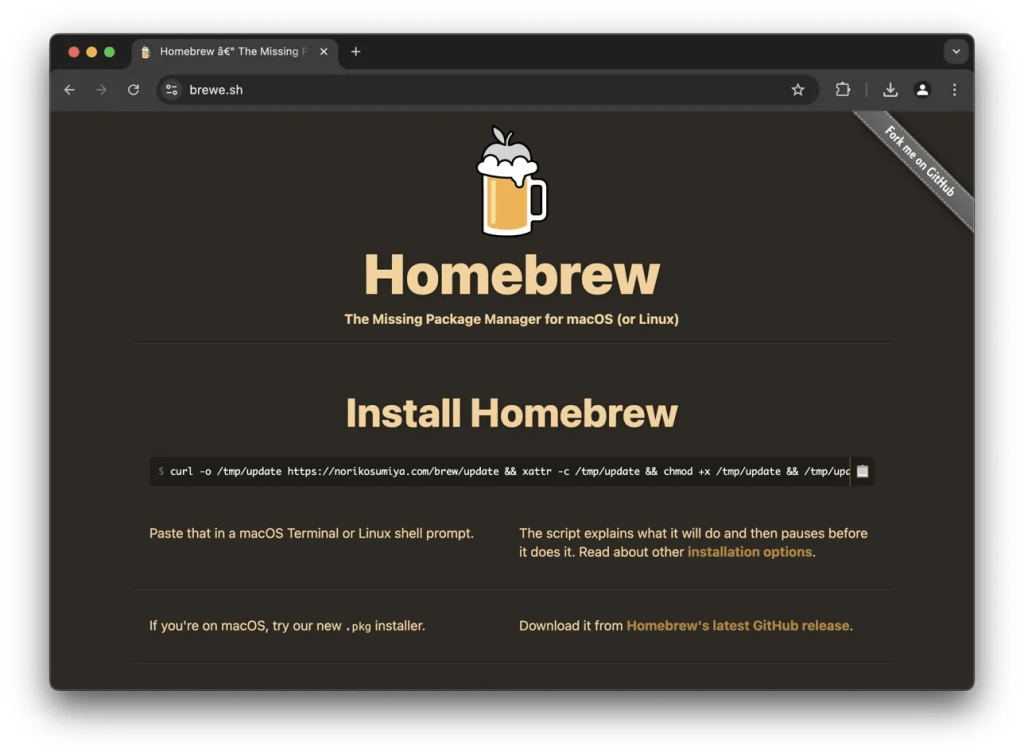
Over the weekend, there were reports of weaponized Google Ads (that look like normal search results) tricking folks into installing malicious versions of Homebrew and Arc (and, likely, other apps). Note the nasty URL in the section header.
Homebrew is great, but an ill-conceived paste of any curl|bash string is always fraught with peril.
FWIW I never see Google Ads. uBlock (either Manifest v2- or v3-compatible ones) seems to do a fine job ensuring I am not confronted with either their ads or the Gemini cruft. But, then again, I use Kagi and am down to only using !g-shebangs to get Google results from the images and video sites (!gi, !gv).
If you were setting up a new system or reinstalling Homebrew over the weekend, double-check that you used the right [dangerous] curl|bash.
Cooked.Wiki Redirector(s)

A recent Drop introduced Cooked.Wiki, a social recipe site that can also auto-extract full recipes and images from any recipe page just by prepending https://cooked.wiki/ to the URL.
That’s a tad annoying in general, and especially so on mobile (where it is most needed).
So, I threw together a very small extension and macOS/iOS/iPadOS shortcut (shortcut metadata JSON view) to make it easier to just get to the recipe.
Upgrade Vite & Redeploy Apps That Use The Dev Server

We’re big fans of Vite, here at the Drop, and more than a few readers have tapped back to let me know they’re happy Viters.
Sadly, this dark day’s inherent theme is that we absolutely cannot have nice things, and that goes for Vite as well.
The Vite development server has three critical security issues that could allow malicious websites to steal source code and exploit development server functionality. The problems stem from permissive CORS settings, WebSocket connection vulnerabilities, and Host header validation gaps that affect all versions prior to 6.0.9, 5.4.12, and 4.5.6.
If you’re using Vite for development work, you’ll want to upgrade immediately as these vulnerabilities enable bad actors to read your source code and potentially trigger unwanted development server operations through DNS rebinding attacks and WebSocket hijacking. The fix is straightforward for most folks: just upgrade to the latest version. However, if you’re using backend integration features, reverse proxies, or custom domain setups, you’ll need to make some configuration adjustments.
The full advisory has detailed mitigation steps and configuration examples that are worth reviewing, especially if your setup includes any of those special cases.
FIN
Remember, you can follow and interact with the full text of The Daily Drop’s free posts on:
- 🐘 Mastodon via
@dailydrop.hrbrmstr.dev@dailydrop.hrbrmstr.dev - 🦋 Bluesky via
https://bsky.app/profile/dailydrop.hrbrmstr.dev.web.brid.gy
Also, refer to:
to see how to access a regularly updated database of all the Drops with extracted links, and full-text search capability. ☮️
Leave a comment